Table of Content
Table of Content
If you thought your cloud environment was airtight, you might want to revisit this thought from a hacker’s perspective. While you are focusing on increasing sales, hackers are continuously scanning cloud services to check for vulnerabilities.
You will never know if your defenses are perfect unless you check for potential issues and bugs. By failing to test them thoroughly, you are opening the environment for security breaches that can lead to potential data loss and compliance risks.
With Cloud Penetration Testing, you are aware of the possible risks and can mitigate them before hackers exploit you. This method simulates an attack on the software to identify vulnerabilities before hackers can attack your system.
This article will take you through the benefits, challenges, and best practices for cloud penetration testing.
Cloud penetration testing involves simulating cyberattacks on your cloud environment to identify and fix security flaws so that hackers don’t exploit them. It also evaluates cloud-specific configurations and access controls to determine weak spots.
You are using the Amazon Web Services (AWS) infrastructure as your cloud service provider. In this case, the cloud penetration testers would test the cloud environment for weak API configurations, rate limits, and permissive access controls.
Penetration testing can help you manage the fast-changing environment and scale your security measures accordingly.
Whether you have hosted your cloud-native applications on major providers like Google Cloud Platform or AWS, you are responsible for their security. Major cloud-based services have in-built tools, but you need to configure and manage them to keep your cloud application secure.
Cloud penetration testing is crucial as it helps you identify the weaknesses before others can.
Your cloud platforms may face issues like misconfigured storage buckets, broad user permissions or exposed APIs. Hackers can take advantage of these issues. You spot these weak points and resolve the issues when you conduct frequent pen tests.
Your business may rely on cloud systems to manage everything from data storage to mission-critical operations. Downtime will cost you revenue and customers. To avoid these breaches that can also damage the reputation of your business, you must conduct cloud penetration testing.
Organizations like yours must adhere to frameworks like GDPR, HIPAA, and ISO 27001 to ensure they incorporate robust data protection practices. Using the penetration testing services, you can determine the risks and mitigate the issues by ensuring compliance.
That’s why cloud penetration testing is crucial to protect your assets in the cloud environment.
The cloud infrastructure is difficult, which increases the complexity of the threat you face. There are different forms of cloud penetration testing, wherein each targets specific risks associated with the cloud system. Let’s look at each of them in detail:
This testing method prioritizes external attacks, simulating how a real-world hacker would exploit your weaknesses. Your testing team can scan open ports, exposed services, and several other entry points that probably allow unauthorized access to cloud resources or networks.
In this testing, you will assume that the attacker has some level of access, from compromised accounts or insider threats. Your goal with this test is to determine how much damage your hackers can do from the inside via lateral movement and data exfiltration.
Your cloud-based application is vulnerable to several issues, such as XSS, authentication problems, and SQL injections. Using this test, you can simulate these attacks on your web applications to determine weak points in the code and configuration that can cause breaches.
APIs connect your internal systems. However, if you don’t secure them properly, these APIs can expose sensitive data or functions. API testing can help you evaluate how well your endpoints can manage input validation and access control when attacked.
Your weakest link may not be a system; it may be a person. This test will mimic phishing attacks, baiting, and pretexting to see if your employees may unknowingly give up their credentials and access to the cloud.
This test focuses on the cloud setup to check the IAM roles, storage configurations, virtual networks, and security group settings. You can learn about the flaws in the cloud infrastructure and whether it can handle real-world attacks.
This test is crucial, especially if you plan to access cloud services using mobile applications. It will check for communication gaps between the app and the cloud, insecure data storage, and broken authentication. It will help protect users and backend systems.
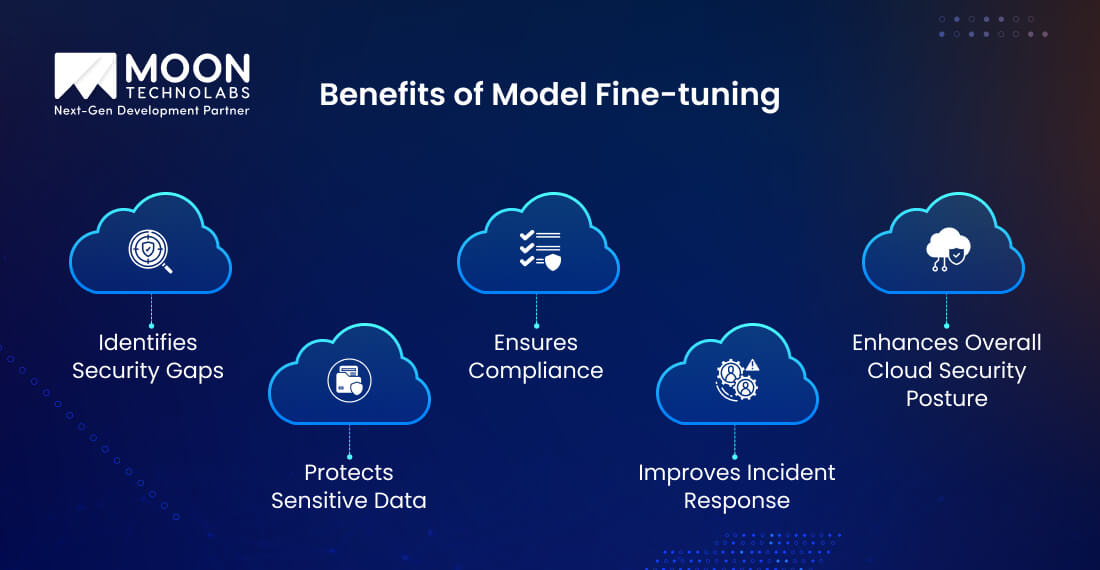
Cloud penetration testing will help you identify flaws and build stronger defences for your system. It has several benefits, such as protecting sensitive data and ensuring compliance, which help deliver a stronger cloud strategy.
You can reveal the vulnerabilities, such as misconfigured settings, unpatched software, and weak passwords, that traditional testing services can miss. Simulating real-world attacks can help you fix these issues before they exploit the software.
Whether your hackers are looking for customer information, your financial records, or internal business communication, you will find them targeting all your sensitive data. With penetration testing, you can secure this data by exposing your cloud’s weak points and leaks.
By actively finding and resolving the risks in your cloud infrastructure through penetration testing, you can ensure adherence to standards like GDPR, HIPAA, and SOC2.
When you understand how attackers infiltrate your systems, strengthening the infrastructure and improving response strategies becomes easier. This prepares your teams for real-world incidents with the right solutions.
This penetration testing model can continuously improve your software. It will ensure your security is aligned with evolving threats, helping enhance cloud security and boost users’ confidence.
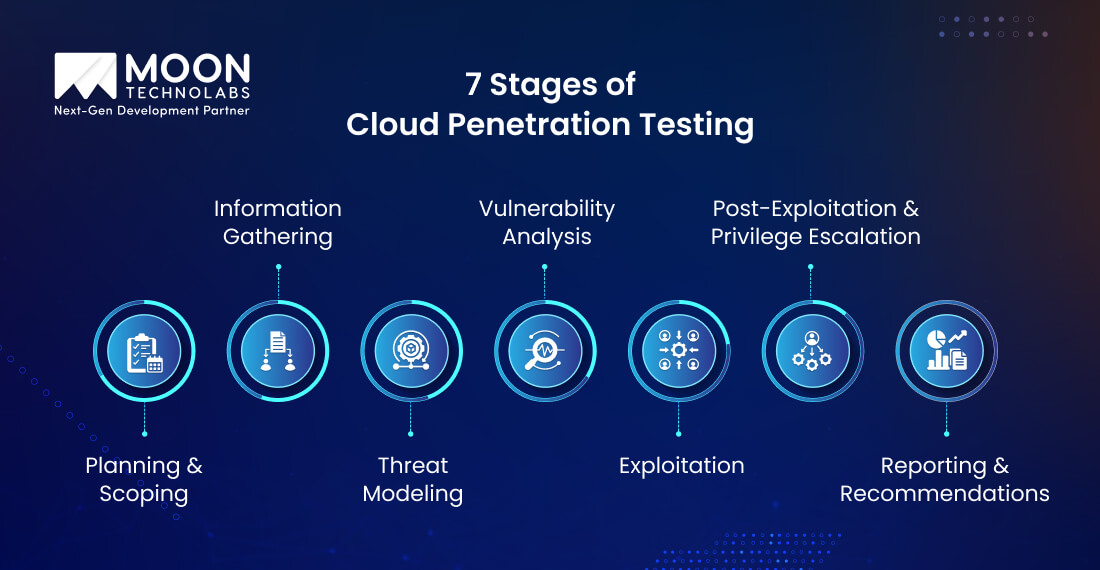
Cloud penetration testing ensures a structured process that helps identify and address weaknesses. Each stage is important in simulating real-world attacks to derive actionable outcomes:
In this phase, you will define the goals, project scope, and rules of engagement. It will also help you define the compliance considerations, the cloud assets to test, the methods you must use, and the expected outcomes. This will ensure you meet security and business objectives on time.
This is the inspection phase, where you collect the known data about the target environment. The testing team will assess the DNS records, employee profiles, cloud asset details, and metadata to map out the cloud infrastructure and determine potential entry points.
The cloud penetration testers will analyze the data to identify how attackers exploit the vulnerabilities. This can help identify high-value assets, assess the potential attack path, and prioritize the targets to simulate real-world scenarios customized for your business.
During this phase, the testers will scan all the cloud resources, such as VMs, APIs, and storage buckets, that are responsible for vulnerabilities or misconfigurations. Several tools and manual methods are used to assess the risk levels and shortlist potential weaknesses.
The testers will attempt to exploit these vulnerabilities identified in the earlier phase in a controlled way. They will gain complete access, exfiltrate the data, and bypass security, mimicking the real attack. Your testing team will be able to determine how the vulnerability will be used against your cloud infrastructure.
Once your testing team can gain access, they will explore how far they can go to damage your cloud infrastructure. For this, the team would access sensitive data, escalate the privileges, and move laterally. Your testing team would look at the worst-case scenario to understand the impact of the breach.
At this point, the testers will compile a comprehensive report that will outline all the findings, determine the risk levels, and provide actionable recommendations. The goal of this phase is to understand the results and provide proper guidance to the development team to strengthen cloud security.
It is possible that there are certain weaknesses present in your cloud infrastructure. Hackers can exploit them if you don’t address and resolve them on time. Here are some of the common vulnerabilities to know:
Cloud storage misconfiguration exposes all your sensitive files to everyone with a single link. An Open S3 bucket is one such cloud storage point wherein you store customer data, internal documents, and backups. Penetration testing can identify these risky setups and secure access permissions to ensure visibility to authorized users.
Identify and assess management roles that contain excessive privileges that give your users more access than they need. Your attackers can exploit this to gain more privileges and move laterally around the cloud. You can detect these broad permissions and apply the principle of least privilege for better control.
Attackers can enter your cloud infrastructure via exposed or unsecured APIs. If you don’t set proper authentication mechanisms or rate limiting, these APIs are abused, and data is leaked. With penetration testing, you can simulate API abuse scenarios to determine security gaps and recommend controls.
Your cloud infrastructure may be using unoptimized default configurations for the open ports, passwords, and access. If you overlook these settings during deployment, you can risk your security. Pen testing can reveal these issues and provide secure configurations.
When data is not encrypted, cybercriminals can steal or intercept it. Cloud penetration testing can identify areas where encryption is missing to ensure end-to-end protection and complete compliance with your cloud infrastructure.
The risk associated with unknown vulnerabilities increases when you use outdated operating systems or libraries. The pen testers identify unpatched components in the cloud stack and simulate attacks to ensure regular updates and patch management.
Access tokens, hard-coded API keys, and database credentials you use for security can go into public repositories. With pen tests, you can expose these issues and simulate them to determine how they are misused. This will help improve your security management and reduce unauthorized access.
If you don’t have proper logging and alerting systems, your attacks may not be detected. Cloud penetration testing can help identify the gaps and improve monitoring systems for faster threat detection.
Here is an at-a-glance comparison between cloud and traditional application penetration testing solutions.
| Factor | Cloud Penetration Testing | Traditional App Penetration Testing |
|---|---|---|
| Deployment Environment | Runs on third-party cloud infrastructure such as AWS or Azure. | It is hosted on the on-premise servers and dedicated infrastructure. |
| Shared Responsibility Model | Security responsibility is shared between the provider and the customer. | The organization is responsible for complete security. |
| API and Endpoint Exposure | APIs, endpoints, and services are exposed externally. | Fewer APIs and exposure is controlled. |
| Storage and Encryption | Secure configurations are needed for cloud storage. Need for cloud-native encryption tools. | Encryption is handled internally with less automation. |
| Access Management | Relies on Identity and Access Management roles and policies. | Uses traditional access and authentication management systems. |
| Third-party Integrations | Integrates with cloud-native services and SaaS tools. | Controlled integrations with external systems. |
| Testing Scope | Cloud provider’s infrastructure is off-limits. | Full stack- app, network, and infrastructure that can be tested. |
Cloud penetration testing is crucial; however, you may face unique challenges that make it more complex than traditional testing. When you understand these issues, it makes it easier for you to plan better:
When you host your software on the cloud, the security responsibilities are split between the cloud service provider and the customer. Testing the app without understanding the model can cause gaps in your outcomes.
Moreover, if you don’t know which areas of the environment you can assess, you may violate the terms.
Your testing team may not have access to the underlying infrastructure, such as physical servers. As a result, you may not be able to deliver in-depth testing outcomes. This means you can only test the customer focus areas while still accounting for provider-side risks.
The cloud environment is continuously evolving, and the services can easily scale on demand. Owing to this fluid nature, it becomes difficult to define a consistent scope while identifying the vulnerabilities. Your penetration test must accommodate ongoing real-time changes.
APIs are indeed the backbone of your cloud application; however, they also increase the attack surface. You need to conduct thorough testing of authentication, rate limits, and other aspects, which requires continuous testing.
Moon Technolabs provides a focused and expert-backed approach to enhancing cloud security for your business software. By using a cloud environment like AWS, Azure, and Multi-cloud, which are suited to your unique needs, they provide custom cloud penetration services.
Using comprehensive cloud security assessments, they go beyond surface-level scans to determine misconfigurations, API, and access issues. If your business is facing compliance issues, our testing team will provide compliance-ready testing solutions to ensure adherence to standards like GDPR, HIPAA, and ISO 27001.
The clear reporting and actionable insights can help you make quick decisions without unnecessary complexities.
The future of cloud penetration testing is a blend of modern technologies and ultimate security models. It is continuously evolving to meet the demands of modern infrastructure.
AI-driven security testing can help you detect vulnerabilities faster and smarter with minimal manual effort. However, you need to invest in continuous testing in constantly evolving and scaling cloud environments.
It is equally important to integrate your infrastructure with the DevSecOps workflows to gain real-time insights into security. Moreover, zero-trust security models will ensure that all access requests are verified before authorizing.
Moon Technolabs offers advanced cloud penetration testing services to identify vulnerabilities and safeguard your business-critical data and operations.
Cloud penetration testing is no longer an option; it is now one of the critical aspects of your cloud security strategy. It helps identify misconfigurations, secure your APIs, and ensure compliance.
It can also help validate the zero-trust models to ensure the organizations are ahead of the evolving threats.
If you want a custom and reliable penetration testing solution for your cloud system, Moon Technolabs is your trusted partner. With our deep expertise and customized solutions, we ensure complete cloud security.
Connect with our team and protect your cloud environment today!
01
02
03
04
05
Submitting the form below will ensure a prompt response from us.