Table of Content
Blog Summary:
APIs are the backbone of modern digital interactions, but are they absolutely protected? This blog guides you through 12 actionable security practices that every developer and tech leader should be aware of. These strategies bulletproof your APIs from the evolving cyber risks. So, let’s discover what it takes to lock down your digital doors and stay one step ahead of hackers
Table of Content
Many articles are filled with sayings that APIs are everywhere. Indeed, that’s true. APIs are all around us. And why not? They are a huge part of the modern software development world.
Whenever a new webpage or app is launched, numerous API calls are made behind the scenes to customize the user experience. APIs also support generic home appliances, such as Amazon Echo, light bulbs, and electricity meters.
However, such prominence also invites risks of cyberattacks. Organizations are increasingly relying on APIs to facilitate smooth integration with vendors, third-party apps, and business partners. A 2024 report by Postman revealed that an average app uses about 26 to 50 APIs.
Hence, modern information and application security strategies are incomplete without proper API security. Let’s examine some API Security Best Practices for implementing effective security measures for your APIs.
Application programming interface (API) security consists of methods to protect APIs. Beyond basic infrastructure security, robust API security requires programmatic controls within the application logic.
Implementing precise API permissions and rules is important to restrict access and ensure that only authorized users consume the intended APIs. Consequently, API security is a fundamental pillar of modern digital enterprises. It safeguards sensitive data transmitted through APIs from unauthorized access.
As we stated earlier, the software development industry relies heavily on application programming interfaces (APIs). They enable different software systems to communicate and share data seamlessly.
They power everything from mobile apps and web applications to IoT devices and cloud based services. However, this widespread adoption makes APIs a prime target for malicious attacks. Hence, businesses need to make APIs more secure than ever.
API security cannot be ignored because if you do so, it can result in serious repercussions for a business and its users:
There are misconceptions that API security and General application security (AppSec) are the same. However, they differ in several ways, and not knowing these differences can pose major risks to your organization.
There are different protection services, such as web app firewalls, API gateways, Identity and Access Management (IAM), and API management tools, that don’t block API attacks. It is indeed a daunting task to secure APIs. Moreover, traditional methods may miss the mark when it comes to managing the technical challenges of the API landscape. You may face the following challenges when opting for API security:
Dynamic & risky outlook: There are tons of APIs being deployed for productivity enhancement. This leads to continuous evolution in the API ecosystem. For this, it’s important to keep a record of the deployed APIs, monitor their performance, and deploy fixes as needed.
Regular testing: unlike app security, where we implement the shift-left strategy, it’s not the same in API security. This approach does not uncover the susceptibilities of your business’s API business logic. On the other hand, developers may unknowingly write insecure code at some point. Therefore, businesses must carry out regular security assessments to detect and block vulnerable API endpoints.
Unique attacks: The API attacks seem equivalent to AppSec, but they are different. In AppSec, there is a possibility of cross-site scripting or SQL injection attacks appearing on numerous apps. Here, there is a separate API for every attack.
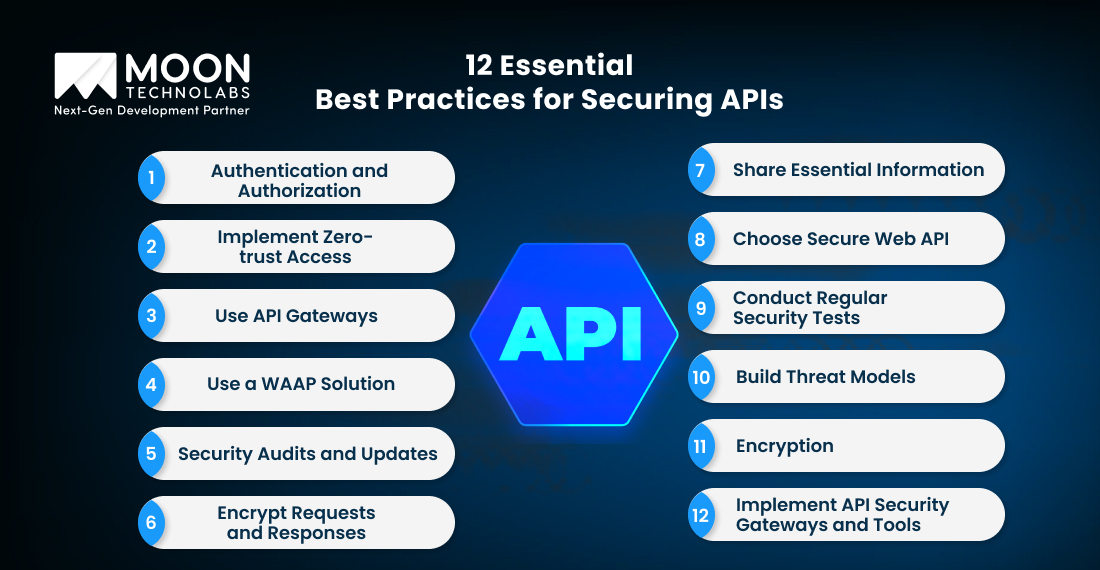
It is recommended to adopt a proactive, lifecycle-integrated approach for strong API security. Follow these 12 proper security measures to deliver comprehensive protection:
To secure your API resources, diligently identify all users and devices that need access. A common method involves requiring client-side applications to present a token with each API request, allowing the service to verify the client’s identity.
Leverage established standards like OAuth 2.0, OpenID Connect, and JSON Web Tokens (JWTs) to authenticate API communication and to establish access control policies.
These standards enable you to define grant types that specify which users, groups, and roles can access particular API resources. For secure machine-to-machine communication, API keys can also be effectively employed.
Crucially, always adhere to the principle of least privilege (POLP). Grant users only the necessary permissions to perform their tasks. For instance, if a user only needs to view a blog or post a comment, assign them solely those specific permissions.
Secure and efficient APIs demand robust access management. Prevent data breaches and DoS attacks by strictly controlling who can access specific API functions. Embrace zero-trust principles by implementing least privilege access, granting users only necessary permissions, and validating every request.
Organizations often design APIs for public consumption, thereby exposing various functions to customers. Consequently, scanning these API endpoints can inadvertently disclose considerable information about their network setup.
To mitigate this risk, API gateways serve as a vital layer of defense, employing request filtering, rate limiting, and API key management to protect APIs from abuse.
Our experts provide real, battle-tested advice to bulletproof your APIs from threats you don’t even see coming.
APIs are susceptible to a variety of cyber threats, ranging from vulnerability exploitation to functional abuse. A web application and API protection (WAAP) solution acts as a crucial safeguard, identifying and preventing these malicious attempts from reaching and compromising APIs.
Beyond core threat detection and blocking, a WAAP often integrates essential security capabilities, such as encryption and robust access management.
Many audits and updates need to be performed to strengthen your API’s security significantly. It allows you to minimize risks but also clearly demonstrates your dedication to protecting user data and valuable assets. Follow the measures below:
You Might Also Like:
The Ultimate API Development Guide: Roadmap to API Brilliance
To safeguard confidential data exchanged through APIs, such as user data and financial records, it’s crucial to prevent eavesdropping. The secure socket layer (SSL) / transport layer security (TLS) protocol addresses this by authenticating the web server and encrypting API traffic.
Therefore, it mitigates the threat of both social engineering and unauthorized interception of network communications.
API responses frequently transmit entire data records instead of just the needed fields, shifting the burden of filtering to the client. This inefficient practice not only degrades performance by increasing response times but also unnecessarily exposes additional API details and resource access information to potential attackers.
Returning only the essential data for each request is a more secure and efficient approach. For instance, providing just the age when requested, rather than the full birthdate.
When it comes to accessing web services via APIs, three main approaches stand out: SOAP, REST, and GraphQL. Each has its way of doing things and different security considerations.
It’s a communication protocol that emphasizes standardization and robust security. It operates at the message level, securing data through digital signatures and encryption directly within its XML structure.
While it supports standard SSL/TLS for secure connections, SOAP goes further with web services security, enabling identity verification through intermediaries, unlike the direct point-to-point security of SSL/TLS.
It also includes built-in mechanisms for error handling. However, SOAP exposes application logic as services rather than raw data, which can make it intricate to implement and might necessitate significant changes to existing applications. SOAP primarily works with XML and HTTP.
It is often referred to as RESTful APIs, an architectural style centered around principles for transmitting data. Security in REST largely depends on access control rules tied to the API’s unique identifiers (URIs), leveraging HTTP methods and URL paths. A key advantage of REST is its flexibility in handling various data formats, including JSON, CSV, and standard HTTP.
Since REST focuses on accessing data directly, it’s generally considered a simpler approach for web service integration. This simplicity often makes REST the preferred choice for web development projects. However, security needs to be actively implemented for data exchanges, deployment, and interactions with clients.
It’s a query language and runtime for APIs designed for flexibility and efficiency, particularly when applications need precise data retrieval. It empowers clients to request exactly the data they need. This makes GraphQL particularly useful for:
Despite its advantages, GraphQL introduces its security challenges. Its ability to handle deeply nested queries can be exploited for Denial-of-Service (DoS) attacks.
Additionally, the single API endpoint (/graphql) can increase the risk of broken object level authorization (BOLA) vulnerabilities if authorization checks at the object or field level are overlooked.
With the rapid proliferation of APIs powering critical business functions, they have become prime targets for cyberattacks. This growing reliance on APIs presents a significant threat to organizations while simultaneously offering a lucrative attack vector for malicious actors.
To gain crucial insight into API vulnerabilities, misconfigurations, and other security weaknesses, consistent security testing and risk assessments are essential. This intelligence empowers security teams to effectively prioritize, develop, and deploy the necessary security measures to manage and mitigate API security risks proactively.
Threat modeling is a crucial process for pinpointing potential weaknesses and attack routes. By anticipating these risks, you can proactively implement targeted security measures and controls to fortify your API ecosystem.
Effective threat models are built by dissecting your API’s components (endpoints, data storage, communication pathways) and scrutinizing how data moves between them.
This analysis informs the development of robust security controls, such as encryption, access restrictions, input validation, and continuous monitoring. Ultimately, it shields your APIs from attacks and data breaches.
Securing your API hinges on encrypting data, and HTTPS with TLS is a primary method for safeguarding communication between clients and servers. This shields sensitive information from interception, tampering, and theft.
Beyond transit, protecting data at rest is vital. Encrypting data in databases, file systems, and other storage using techniques like transparent data encryption, column-level encryption, or file-level encryption hinders unauthorized API access and data breaches if storage systems are compromised.
A strong key management strategy is paramount when employing encryption. Securely generate, store, and manage encryption keys, keeping them separate from the encrypted data and restricting access to authorized personnel. Regular key rotation further reduces the risk of compromise.
An API security gateway is a dedicated software or hardware component designed to secure APIs against external vulnerabilities. Operating as a proxy, it intercepts requests to the API, enforces predefined security policies, and performs critical functions such as authentication, authorization, and threat monitoring of API traffic.
Implementing security at the gateway level decouples these concerns from the API itself, enhancing scalability and manageability. Key security functionalities commonly provided include strong authentication mechanisms, authorization controls, rate-limiting policies, and encryption protocols.
Moreover, API security gateways facilitate comprehensive monitoring and logging of API interactions, enabling detailed analysis for identifying usage patterns and potential security anomalies, thereby contributing to an enhanced security framework for your APIs.
Securing an API involves various factors that influence the overall cost, and it’s important to understand that this isn’t just a one-time expense but an ongoing investment. The cost depends on the API’s complexity, the level of protection required, and whether you handle the process in-house or outsource it to third-party services.
One of the primary costs is the time and effort required for API development. Developers need to implement essential security measures such as data encryption, input validation, rate limiting, authentication, and authorization. Depending on the scope and expertise involved, this process can cost anywhere from $1,000 to over $10,000.
In addition, security tools and services significantly contribute to the total cost. API gateways, such as AWS API Gateway, Apigee, or Kong, provide features like throttling, monitoring, and security policies, and typically charge around $3 to $10 per million API calls.
Authentication services like Auth0 or Firebase Authentication may start free, but can cost around $100 per month for advanced features. For added protection, many organizations also use web application firewalls (WAFs), which can cost between $20 and $200 per month.
Monitoring and logging tools are also vital, as they help detect and respond to suspicious activities in real time. Popular services like Datadog, Splunk, and AWS CloudWatch can cost between $10 and $300 or more per month, depending on usage.
Furthermore, regular penetration testing and security audits, which are crucial for identifying vulnerabilities, can cost anywhere from $5,000 to $30,000 or more per test.
Moreover, ongoing maintenance is an essential part of API security. This includes tasks like patch management, rotating access tokens, managing encryption keys, and keeping up with compliance requirements. While the cost for this varies widely, it often involves internal staffing time or additional service costs.
Our experts will implement industry-leading security practices to safeguard your APIs from unauthorized access, data breaches, and cyber threats.
You’re spot on! APIs unlock a wealth of possibilities for organizations to enhance service delivery, deepen customer engagement, and boost both productivity and profits. However, this potential is realized only through robust security measures.
Building an API with quality and security is crucial, not an afterthought. Contact our experts now to build a high-quality and secure API.
01
02
03
04
05
Submitting the form below will ensure a prompt response from us.